Harvest raw materials hunt fish and farm to survive. Blocks ultimate nightmare is that terrorists could somehow get access to the smallpox viruses being kept on ice at the.

Wireless Lan Implications Problems And Solutions Security Vulnerabilities Cisco Press
Ieeexplore Ieee Org
Rogue Access Points Article Khan Academy
Following are 10 safety tips to help you guard against high-tech failure.

How to protect against rogue access points. Deploy adaptive access and session controls for all apps. What makes a rogue access point rogue. Low-level highlights of the rogue class include Expertise and Cunning Action.
Acrobatic Assist Ex You can expend an attack of opportunity to perform an aid another action to assist an adjacent allys Acrobatics check so long as he makes the check as part of movement that passes through your space or an adjacent space. A years worth of data shows that protection against bad outcomes remains robust even though protection against infection declines substantially after about 6 months. Once you gain access to a circle spell you always have it prepared and it doesnt count against the number of spells you can prepare each day.
However the Omniversal Guardian named Roma restored the X-Men to life and freed the Adversary under the notion that there could be no order without chaos. It also reduces the fallout of compromised accounts and can protect against the damage done by rogue users. 8 hit points is hard if youre in melee.
Cisco Meraki defines a rogue access point as an AP that is both seen on the LAN and is broadcasting SSIDs that are visible to the APs that make up the corporate wireless infrastructure. Rogue is a long-time central character in the X-Men world within the Marvel Universe. Assess the security posture of your cloud environments.
The 370 Series APs also provide sealed connector interfaces to protect against dust and moisture. The artificer-rogue is a skill monkey who can eke out more damage from their attacks and maneuver around the battlefield with ease. NortonLifeLock offerings may not cover or protect against every type of crime fraud or threat we write about.
Her beginnings were as a simple villain being led on by Mystique. Available as its own stand-alone unit or as a conversion kit for an existing Rogue Z Hyper the Donkey enables athletes to perform reverse hyperextensions rows back and hip extensions GHD sit-ups and glute-ham raises on the same piece. If left connected either type of rogue device can pose a security threat.
Zero-touch provisioning Access points can be factory-shipped and zero-touch provisioned through Aruba Central or AirWave using a cloud-based service to reduce deployment time centralize configuration and manage inventory. The Rogue is not a front-line Defender by any means even if you go for the Ruffian Racket to get medium armor. To successfully protect an enterprise network a Wireless Intrusion Prevention System WIPS should provide powerful wireless intrusion scanning capabilities enabling detection and classification of different types of wireless threats including rogue access points and wireless hackers.
Indoor APs feature a radio dedicated to full-time scanning rogue AP containment and automatic RF optimization. Our goal is to increase awareness about cyber safety. We have an aggressive global approach to deny our enemies access to WMD-related materials with a particular focus on weapons-usable fissile materials fabrication expertise methods of transport sources of funds and other capabilities that facilitate the execution of a WMD attack.
Rogue APs can be further classified into web robots bots and. Learn how to protect yourself and your loved ones from scams. Protect sensitive information and activities automatically by implementing policies.
After these are completed focus on these additional deployment objectives. Change the default password on your consumer-grade routers and wireless access points. Rogue is a fictional character appearing in American comic books published by Marvel Comics commonly in association with the X-MenThe character debuted in Avengers Annual 10 as a villain but she joined the X-Men soon thereafter.
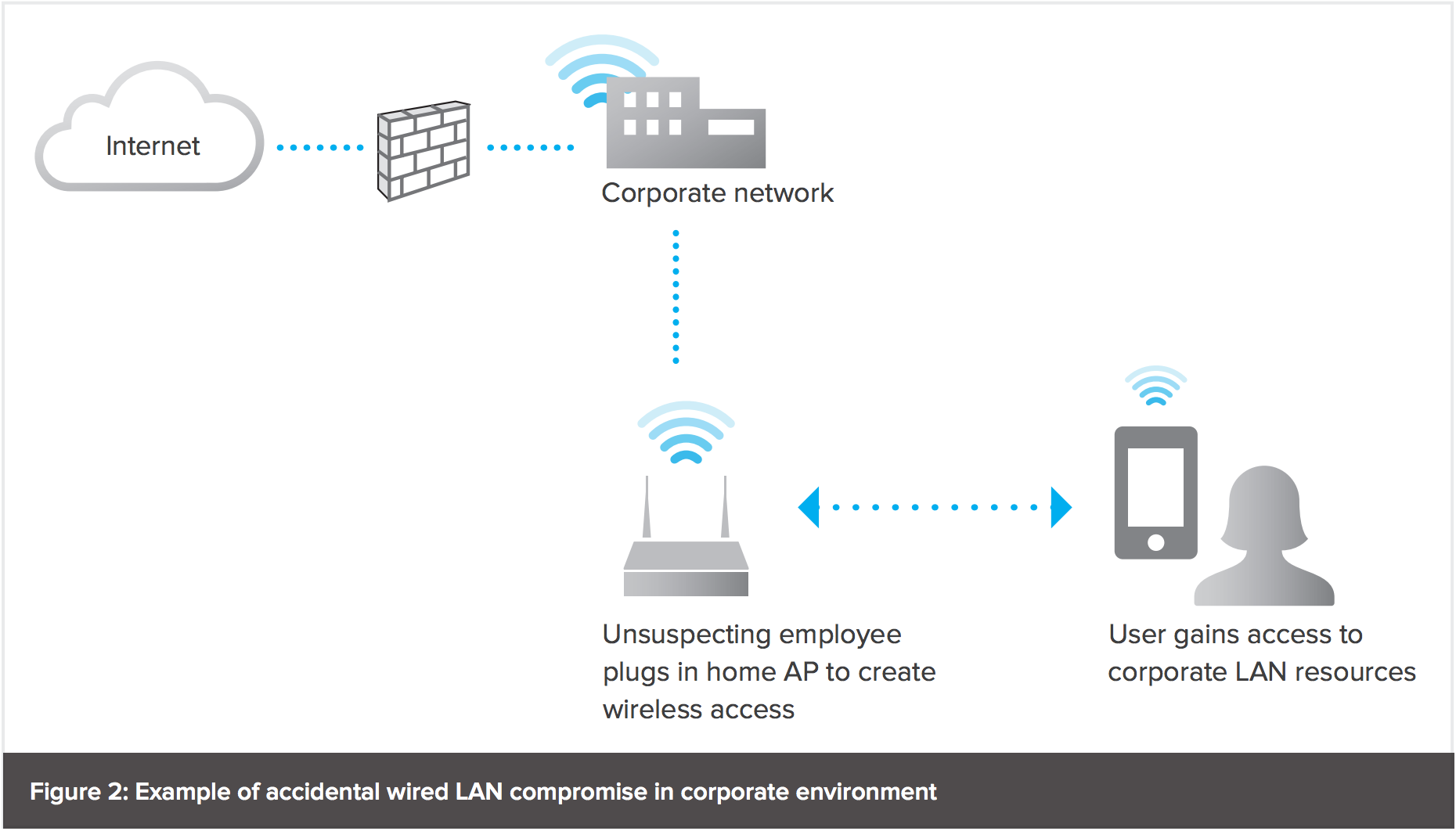
Rogue devices can be wireless access points sometimes referred to as rogue APs or end-user computers rogue peers. He points out that although the. This is a frequently overlooked part of user management.
Integrated network access control NAC provides end-user anti-virus scanning for accurate client device posture assessment to protect your wired and wireless network against virus infections. Friends Against Scams is a National Trading Standards Scams Team initiative which aims to protect and prevent people from becoming victims of scams by empowering people to take a stand against scams. The Rogue Donkey is an entirely new beast.
Introducing Assassins Creed Rogue the darkest chapter in the Assassins Creed franchise yet. An all-in-one hybrid of our Z Hyper reverse-hyper machine and Abram GHD 20 glute-ham developer. While rogue hackers get most of the press.
A rogue corrupted DNS server however. Follow your own creed and set off on an extraordinary journey through New York City the wild river valley and far away to the icy cold waters of the North. Protect and guide your people as you forge a town from untamed wilderness at the edge of the known world.
As Shay you will experience the slow transformation from Assassin to Assassin Hunter. Deny terrorists access to the materials expertise and other enabling capabilities required to develop WMD. Additionally whenever you use the aid another action to assist an ally in making an.
Having carefully defined user roles and access rules will limit any mistakes that can be made. You also need to make the attack using Strength rather than Dexterity which is a hard way to build a rogue most of the time. Rogue is part of a subspecies of humans called mutants who are born with superhuman abilitiesRogue has the involuntary ability to absorb and sometimes also.
Roguelike or rogue-like is a subgenre of role-playing video games characterized by a dungeon crawl through procedurally generated levels turn-based gameplay grid-based movement and permanent death of the player characterMost roguelikes are based on a high fantasy narrative reflecting their influence from tabletop role playing games such as Dungeons Dragons. After gaining access into the Starlight Citadel the X-Men battled the Adversary and after Rogue absorbed his power and opened a portal to seal him in gave their lives to imprison the Adversary with a spell cast by Forge. Be sure to pad your hit points with high Constitution and strongly consider Toughness if you plan to fight in melee.
As with the fighter even a small dip can be all you need to make your character feel unique and better at what they do best. If rogue politicians or terrorists. However on a class as frail as the Rogue its extremely dangerous to grant Advantage against yourself and there are plenty of other ways to gain reliable access to Advantage and Sneak Attack.
Produce crafted items to trade consume equip and fight with as you battle for your survival against the elements and outside threats. Strengthen protection against cyber threats and rogue apps. Talent Prerequisites Benefits Source.
Access to all equipment. Internet-only guest Wi-Fi in just one click. If you gain access to a spell that doesnt appear on the druid spell list the spell is nonetheless a druid spell for you.
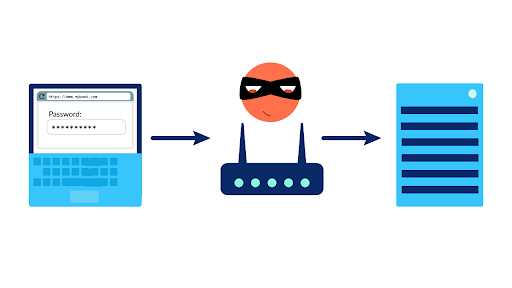
So its very clear that rogue access points are something we need to protect our business critical WLAN and networks from.
Security Threats Chapter 8 Wireless Network Security Protecting Information Resources Wireless Networks First Step Networking Etutorials Org
Rogue Access Point Cisco Meraki Blog
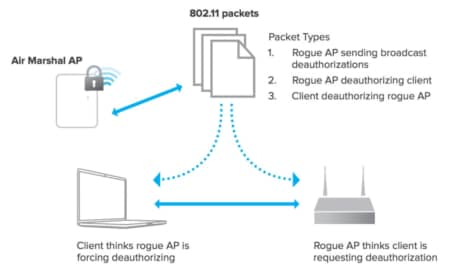
Air Marshal Cisco Meraki

Air Marshal Cisco Meraki

Pdf Rogue Access Point Detection System In Wireless Lan Semantic Scholar
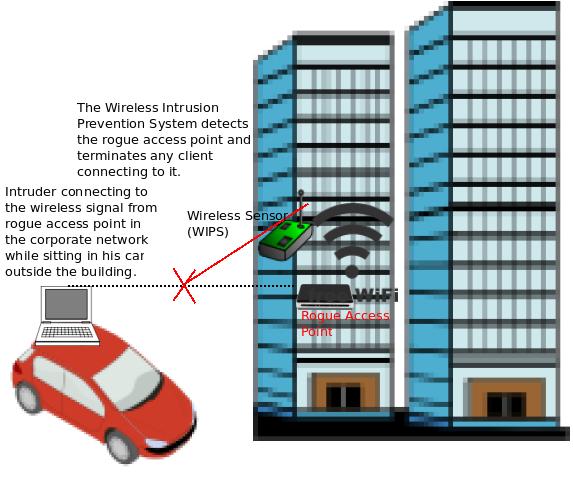
What Are Rogue Access Points And How Rogue Access Points Are Detected Blocked Excitingip Com

Ap Spoofing In Ieee 802 11 Network Hossain M

Mitigating Rogue Access Points In Corporate Environments Design