Patent 1310719 a cipher based on teleprinter technology. The encode method created the cipher text with a key specifying the number of columns and we have printed each cipher text by reading through each column.
Code 4 Life Columnar Transposition Cipher Without Key

Introduction To Cryptography Ppt Video Online Download
Another Symmetric Key Cipher Is Columnar Chegg Com
It includes various techniques like the Rail Fence technique Simple columnar transposition technique simple columnar transposition technique with multiple rounds Vernam cipher and book Cipher to encrypt the plain text in a secure way.
Columnar transposition cipher program in c. The Rail fence cipher also called zigzag cipher is. Explanation - In the above code we have created a function named split_len which spitted the pain text character placed in columnar or row format. The next one-time pad system was electrical.
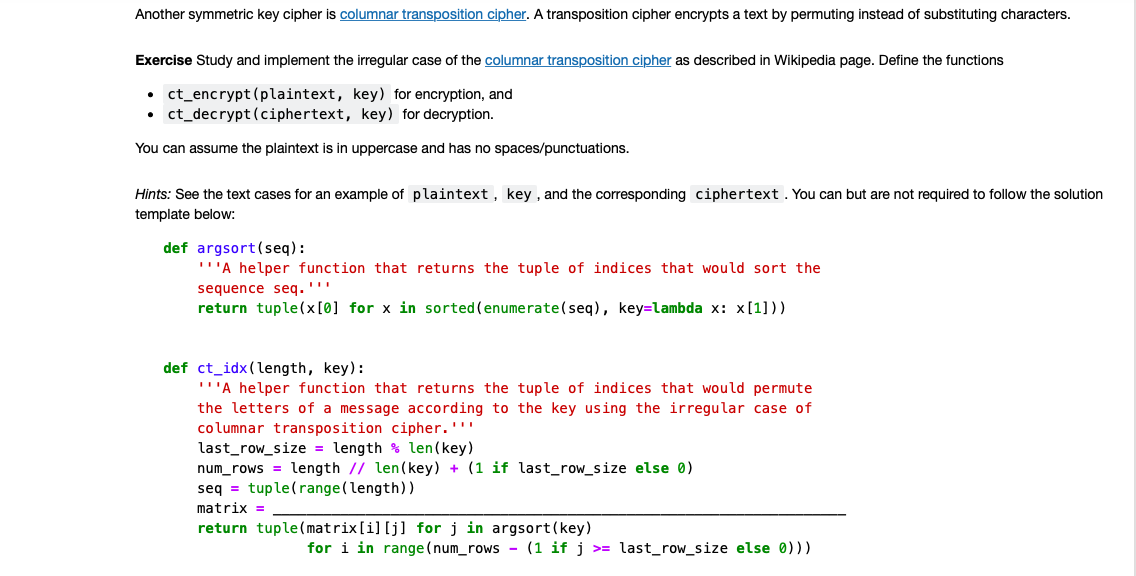
The cipher text for message Transposition Cipher with key as 6 is fetched as Toners raiCntisippoh. In 1917 Gilbert Vernam of ATT Corporation invented and later patented in 1919 US. The Columnar Transposition Cipher is a form of transposition cipher just like Rail Fence CipherColumnar Transposition involves writing the plaintext out in rows and then reading the ciphertext off in columns one by one.
Difference Between Substitution and Transposition Cipher. Observe the following code for a better understanding of decrypting a transposition cipher. Frank Miller in 1882 was the first to describe the one-time pad system for securing telegraphy.
In cryptography a Caesar cipher also known as Caesars cipher the shift cipher Caesars code or Caesar shift is one of the simplest and most widely known encryption techniques. Transposition Cipher Solver This is a little tool to help decrypt transposition ciphers in the horizontal column switching format. For the decryption the reverse substitution has to be performed.
May 27 2020 Substitution Cipher Solver Algorithm for solving simple monoalphabetic substitution ciphers. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabetFor example with a left shift of 3 D would be replaced by A E. In the rail fence cipher the plain-text is written downwards and diagonally on successive rails of an imaginary fence.
Used by the Germans in WWI. When we reach the bottom rail we traverse upwards moving diagonally after reaching the top rail the direction is changed again. Each character in a message was electrically combined with a character on a punched paper tape key.
In this chapter you will learn the procedure for decrypting the transposition cipher. Note - The transposition technique is meant to be a significant improvement in. However in transposition cipher we just rearrange the plaintext letters in a different.
In substitution cipher we replace each letter of the plaintext with another letter symbol or number. Decryption of Transposition Cipher. Given a plain-text message and a numeric key cipherde-cipher the given text using Columnar Transposition Cipher.
Nihad Ahmad Hassan Rami Hijazi in Data Hiding Techniques in Windows OS 2017. A special cipher somewhat based on the Caesarian shift but you change the value of N with each letter and it is all based on a passphrase. In a transposition cipher the order of the alphabets is re-arranged to obtain the cipher-text.
A double columnar transposition cipher that uses the same key but adds a number of pad characters.

A Hybrid Cryptosystem Based On Vigenere Cipher And Ijater
Chapter 7 Encrypting With The Transposition Cipher

Columnar Transposition Cipher Technique Encrypt Plain Text Message Cipher Decipher Youtube
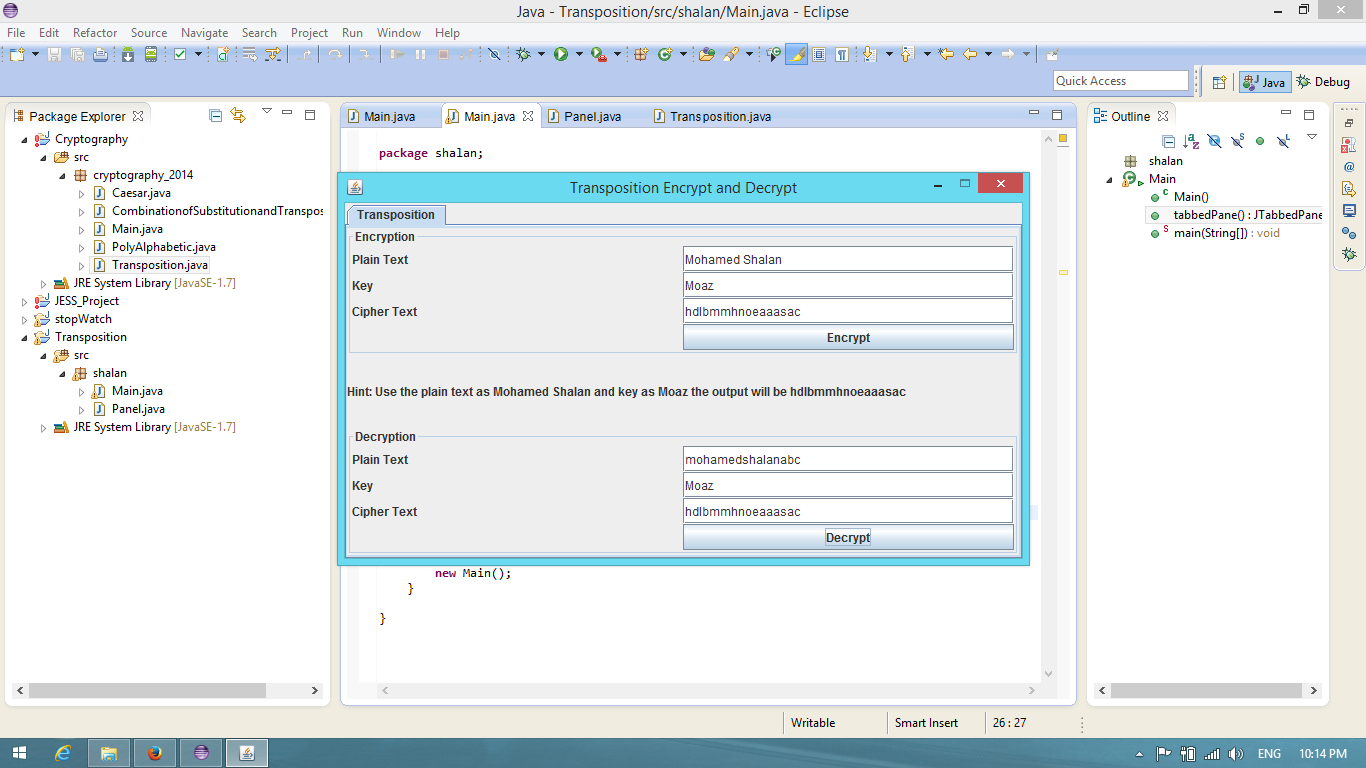
Github Sh3lan93 Columnar Transposition Java A Simple Java Gui Program That Take An Input From User From A To Z Regardless Of The If The String Is In Lowercase Or Uppercase Or

What Is Transposition Technique In Cryptography Binary Terms
Ijsr Net
Nku Edu

To Implement Columnar Transposition Cipher Encryption Decryption In C With Output Image